To be completed by the original poster:
CMS Version
release-3.0.7 (Docker version)
Player Type
Xibo for Linux
Player Version
1.8 R6
Issue
I have my CMS server on AWS sitting behind an application load balancer which listens to port 443 and forward the request to the CMS server on port 80.
I have configured Settings-custom.php file as the following:
$authentication = new \Xibo\Middleware\SAMLAuthentication();
$samlSettings = array (
'workflow' => array(
// Enable/Disable Just-In-Time provisioning
'jit' => true,
// Attribute to identify the user
'field_to_identify' => 'UserName', // Alternatives: UserID, UserName or email
// Default libraryQuota assigned to the created user by JIT
'libraryQuota' => 0,
// Initial User Group
'group' => 'users',
// Home Page
# 'homePage' => 'icondashboard',
// Enable/Disable Single Logout
'slo' => false,
// Attribute mapping between XIBO-CMS and the IdP
'mapping' => array (
'UserID' => '',
'usertypeid' => '',
'UserName' => 'USER_NAME',
'email' => 'EMAIL',
)
),
// Settings for the PHP-SAML toolkit.
// See documentation: https://github.com/onelogin/php-saml#settings
'strict' => false,
'debug' => true,
'idp' => array (
'entityId' => 'https://myidpprovider.com',
'singleSignOnService' => array (
'url' => 'https://myidpprovider.com/api/saml2/v1/sso',
),
'singleLogoutService' => array (
'url' => 'https://myidpprovider.com/api/saml2/v1/logout',
),
'x509cert' => xxxxxxx
'NameIDFormat' => 'urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified',
),
'sp' => array (
'entityId' => 'https://xibo.mydomain.com',
'assertionConsumerService' => array (
'url' => 'https://xibo.mydomain.com/saml/acs',
),
'singleLogoutService' => array (
'url' => 'https://xibo.mydomain.com/saml/sls',
),
# 'NameIDFormat' => 'urn:oasis:names:tc:SAML:2.0:nameid-format:emailAddress',
'x509cert' => '',
'privateKey' > '',
),
'security' => array (
'nameIdEncrypted' => false,
'authnRequestsSigned' => false,
'logoutRequestSigned' => false,
'logoutResponseSigned' => false,
'signMetadata' => false,
'wantMessagesSigned' => false,
'wantAssertionsSigned' => false,
'wantAssertionsEncrypted' => false,
'wantNameIdEncrypted' => false,
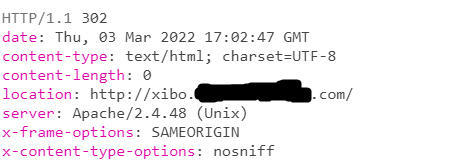
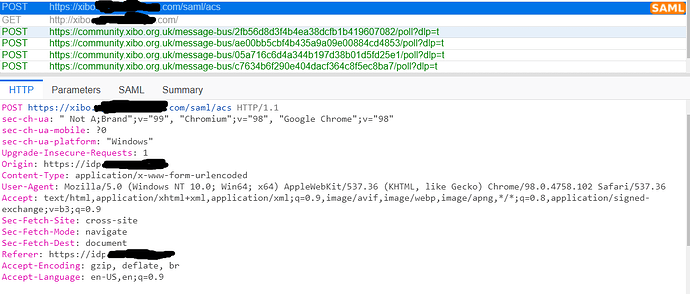
when I navigate to https://xibo.mydomain.com/ , Xibo is redirecting to idp and passes http://xibo.mydomain.com/ as the RelayState instead of https://xibo.mydomain.com/, so idp is returning it to xibo cms server after authenticating me and supposed to redirect me to the page I was trying to access, BUT the relay state has http instead of https for some reason
The authentication is happening correctly from idp side. idp POSTs the SAMLResponse to https://xibo.mydomain.com/saml/acs with http://xibo.mydomain.com/some-url as the Relaystate. Idp then redirects me to the RelayState, here is my problem: the request times out because the load balancer is not listening on port 80. So why xibo cms uses http instead of https for the RelayState. any idea why is that happening? is it a bug?
the screenshots below is from saml-tracer plugin: