Thanks @alex for your follow up.
actually I changed it to test because I can’t map a new user. In fact, for authentication via ADFS to work, an adjustment had to be made to the setting file because currently the new version of ADFS requires a certX509 and the key for the CMS. here is a configuration that works.
<?php
# If you need to add custom configuration settings to the CMS settings.php file,
# this is the place to do it.
# For example, if you want to configure SAML authentication, you can add the
# required configuration here
$authentication = new \Xibo\Middleware\SAMLAuthentication();
$samlSettings = array (
'workflow' => array(
// Enable/Disable Just-In-Time provisioning
'jit' => true,
// Attribute to identify the user
'field_to_identify' => 'UserName', // Alternatives: UserID, UserName or email
// Default libraryQuota assigned to the created user by JIT
'libraryQuota' => 1000,
// Initial User Group
'group' => 'Users',
// Home Page
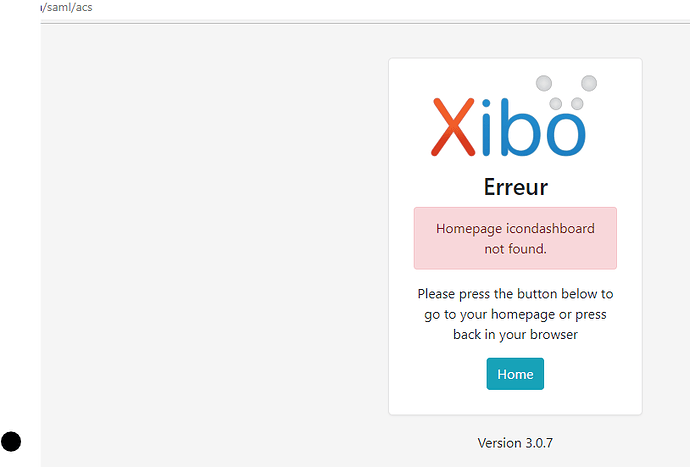
'homePage' => 'icondashboard.view',
// Enable/Disable Single Logout
'slo' => 'true',
// Attribute mapping between XIBO-CMS and the IdP
'mapping' => array (
'UserID' => '',
'usertypeid' => '',
'UserName' => 'uid',
'email' => 'mail',
// 'firstName' => 'surname',
// 'lastName' => 'givenname',
)
),
// Settings for the PHP-SAML toolkit.
// See documentation: https://github.com/onelogin/php-saml#settings
'strict' => false,
'debug' => true,
'idp' => array (
// Identifier of the IdP entity (must be a URI)
'entityId' => 'https://mycms.com/saml/acs',
'singleSignOnService' => array (
// URL Target of the IdP where the Authentication Request Message will be sent
'url' => 'https://myadfs.com/adfs/ls',
),
'singleLogoutService' => array (
// SLO endpoint info of the IdP.
'url' => 'https://myadfs.com/adfs/ls/',
),
'x509certMulti' => array(
'signing' => array(
0 => 'adfscert',
),
'encryption' => array(
0 => 'adfscert',
)
),
),
'sp' => array (
// Identifier of the SP entity (must be a URI)
'entityId' => 'https://mycms.com/saml/acs',
// Specifies info about where and how the <AuthnResponse> message MUST be returned to the requester, in this case our SP.
'assertionConsumerService' => array (
// URL Location where the <Response> from the IdP will be returned
'url' => 'https://mycms/saml/acs',
),
// Specifies info about where and how the <Logout Response> message MUST be returned to the requester, in this case our SP.
'singleLogoutService' => array (
// URL Location where the <Response> from the IdP will be returned
'url' => 'https://mycms/saml/sls',
),
// Specifies the constraints on the name identifier to be used to represent the requested subject.
// Take a look on lib/Saml2/Constants.php to see the NameIdFormat supported.
'NameIDFormat' => 'urn:oasis:names:tc:SAML:2.0:nameid-format:emailAddress',
'x509cert' => 'mycmscert',
'privateKey' => 'mycmskey',
),
'security' => array (
'nameIdEncrypted' => false,
'authnRequestsSigned' => false,
'logoutRequestSigned' => true,
'logoutResponseSigned' => true,
'signMetadata' => false,
'wantMessagesSigned' => false,
'wantAssertionsSigned' => false,
'wantNameIdEncrypted' => false,
'lowercaseUrlencoding' => true,
)
);
?>
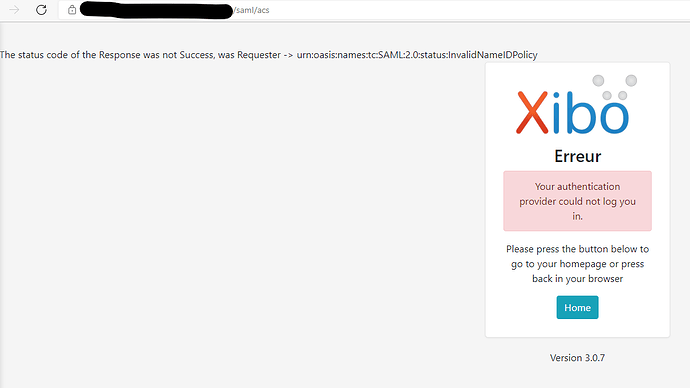
however this setting only allows me to authenticate a user who already exists on the CMS. he can connect via ADFs and disconnect via ADFS too.
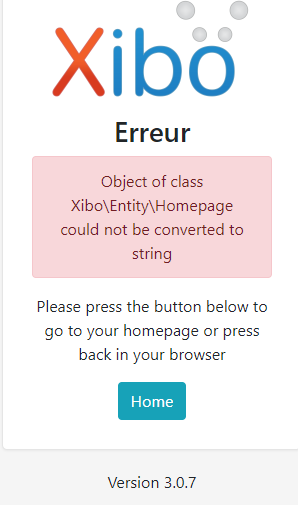
for a new user that I want to create at the same time as his authentication, I have an error message.
yet the ADFS sends me all the required fields.
I wonder if anyone had the same error at JIT or I have a config error thanks